So you have a wireless connection network at home, but your connection is too slow for a few days. why what is the reason ?
Your connection can be used by anyone without the consent of the wireless network router, there are many ways within the Hawk.
How do you know if someone is using your wireless network connection?
This is the best trick for your computer lets begin to main topic,
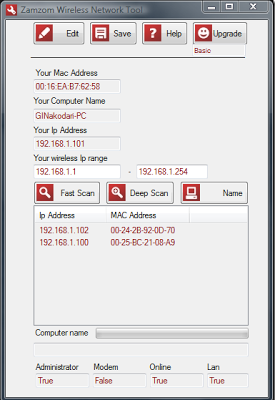
Even if your not a computer geek(computer expert) Still you can trace who is accessing your wifi network are not .Zamzom wireless network tool can scan a quick one for you free access. Only, it is fast to load, and you can hit the scan is connected to your WAN IP and MAC addresses of each computer shows.
You can also do a deep scan, but a fast scan, most consumers will be sufficient. It is, but you can also connect to the Pro version (which cost a few bucks) The name of the computer can be upgraded. You can block the IP address from your router, you can easily through, do not need to know the name of the computer.
Http :/ / www.zamzom.com/ offered free from the new wireless network tool
Your connection can be used by anyone without the consent of the wireless network router, there are many ways within the Hawk.
How do you know if someone is using your wireless network connection?
This is the best trick for your computer lets begin to main topic,
Even if your not a computer geek(computer expert) Still you can trace who is accessing your wifi network are not .Zamzom wireless network tool can scan a quick one for you free access. Only, it is fast to load, and you can hit the scan is connected to your WAN IP and MAC addresses of each computer shows.
You can also do a deep scan, but a fast scan, most consumers will be sufficient. It is, but you can also connect to the Pro version (which cost a few bucks) The name of the computer can be upgraded. You can block the IP address from your router, you can easily through, do not need to know the name of the computer.
Http :/ / www.zamzom.com/ offered free from the new wireless network tool
For Further Reading,